information security layers
-
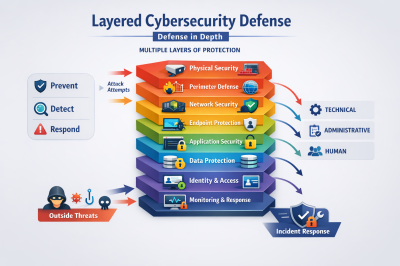
Layering in Cybersecurity Defense Systems: A Complete Defense-in-Depth Tutorial
Ashwani Kumar
Limited Time Offer! For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly. Master…

Recent Posts
- Overview of Certified Kubernetes Administrator (CKA) Certification
- How to Install and Configure XAMPP on Ubuntu 24 Server (Latest Version – 2026 Complete Guide)
- Mastering the Google Cloud Professional DevOps Engineer
- Mastering Azure Cloud Security: The AZ-500 Path
- Why AZ-400 is Essential for Global Cloud Engineering Roles
Categories
- Ai 2
- AI Blogging 2
- AiOps 1
- ajax 1
- Android Studio 1
- Antimalware 1
- Antivirus 1
- Apache 2
- Api 4
- API Security 1
- Api Testing 1
- APK 1
- Aws 2
- Bike Rental Services 9
- ChatGPT 1
- Code Linting 1
- Composer 2
- cPanel 1
- Cyber Threat Intelligence 1
- Cybersecurity 1
- Data Loss Prevention 1
- Database 1
- dataops 1
- Deception Technology 1
- DeepSeek 2
- Devops 14
- DevSecOps 11
- DevTools 1
- Digital Asset Management 17
- Digital Certificates 1
- Docker 5
- emulator 1
- Encryption Tools 1
- Endpoint Security Tools 1
- Error 1
- facebook 1
- Firewalls 2
- Flutter 12
- git 5
- GITHUB 6
- Google Antigravity 1
- Google play console 3
- Google reCAPTCHA 1
- Gradle 2
- Guest posting 1
- health and fitness 1
- IDE 1
- Identity and Access Management 1
- Incident Response 1
- Instagram 1
- Intrusion Detection and Prevention Systems 1
- jobs 1
- Joomla 1
- Keycloak 15
- Laravel 40
- Law News 1
- Lawyer Discussion 1
- Legal Advice 1
- Linkedin 1
- Linux 20
- Livewire 5
- Medical Tourism 1
- MlOps 2
- MobaXterm 1
- Mobile Device Management 1
- Multi-Factor Authentication 1
- MySql 8
- Network Traffic Analysis tools 1
- Paytm 1
- Penetration Testing 1
- php 24
- PHPMyAdmin 2
- Quora 1
- SAST 1
- SecOps 1
- Secure File Transfer Protocol 1
- Security Analytics Tools 1
- Security Auditing Tools 1
- Security Information and Event Management 1
- Seo 1
- Server Management Tools 2
- Single Sign-On 1
- Site Reliability Engineering 1
- soft 404 1
- software 2
- SuiteCRM 3
- SysOps 1
- Threat Model 1
- Twitter 1
- ubuntu 1
- Uncategorized 665
- Virtual Host 1
- Virtual Private Networks 3
- VPNs 1
- Vulnerability Assessment Tools 1
- Web Application Firewalls 1
- Windows Processor 4
- Wordpress 2
- WSL Windows Subsystem for Linux 20
- X.com 1
- Xampp 11
- Youtube 1
Tags
#CareerGrowth #CICD #CI_CD #CloudNative #DevOps #DevOpsCareer #DevOpsSkills #DevOpsTraining #DevSecOps #ITTraining #Kubernetes #SoftwareDevelopment #SRE Best DAM Software DAM DAM Software Devops DevSecOps Digital Asset Management Error flutter How Keycloak laravel Laravel Error Linux php Troubleshooting Why Xampp