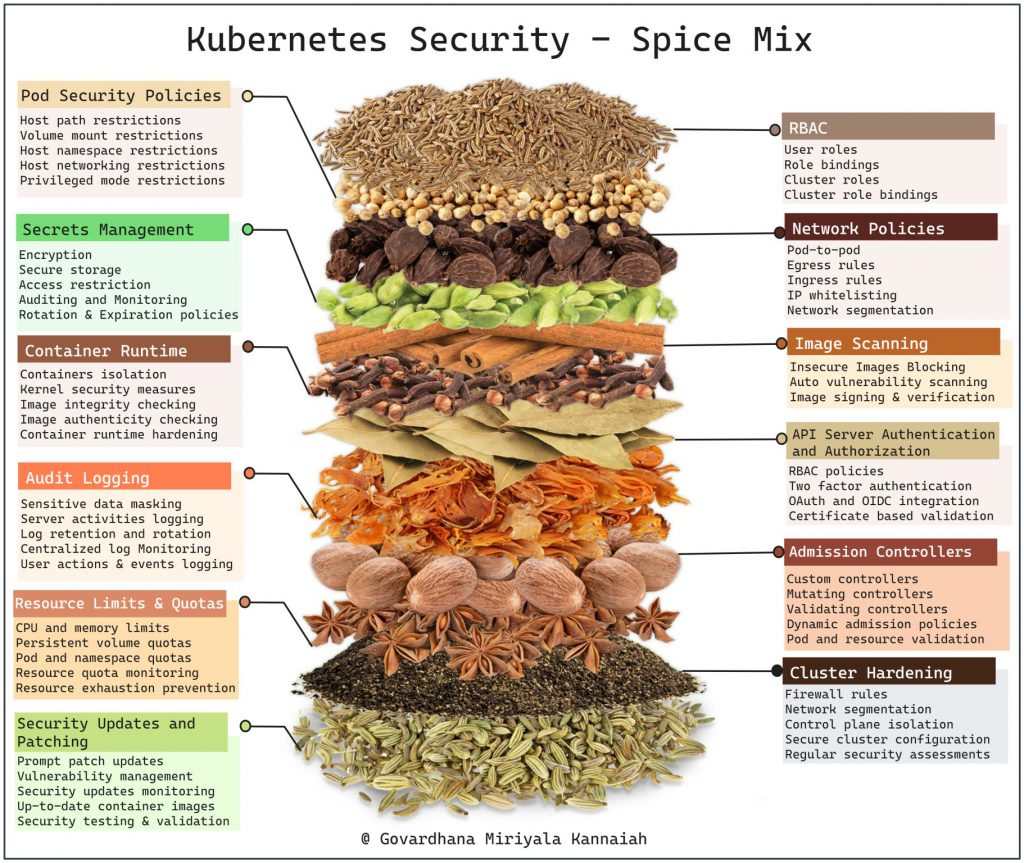
Implementing Kubernetes security requires the use of various tools and solutions that can help you monitor, detect, and mitigate security risks. Here are some popular tools for implementing Kubernetes security:
Kubernetes Security Policies and Controls:
- Kubernetes Security Context: Allows you to define security parameters for Pods and containers.
- Kubernetes Network Policies: Enable you to control network traffic between Pods and namespaces.
- Kubernetes Pod Security Policies: Enforce security policies on Pods and control their security context.
Container Image Scanning and Vulnerability Management:
- Clair: An open-source vulnerability scanner for container images.
- Trivy: A simple and comprehensive vulnerability scanner for containers and images.
- Anchore Engine: Scans and analyzes container images for vulnerabilities and policy violations.
- Aqua Security: Provides container security and compliance solutions with image scanning capabilities.
Kubernetes Audit Logging and Monitoring:
- Falco: A behavioral activity monitor that alerts on suspicious behavior in Kubernetes.
- Sysdig Secure: Offers runtime security, threat detection, and incident response for Kubernetes.
- Prometheus: A monitoring system that can be used to monitor Kubernetes clusters and collect metrics.
- ELK Stack (Elasticsearch, Logstash, Kibana): Enables log collection, analysis, and visualization for Kubernetes.
Kubernetes Configuration Management and Compliance:
- kube-bench: A tool that checks Kubernetes configurations against security best practices.
- kube-score: Evaluates the security and efficiency of Kubernetes deployments.
- kube-hunter: Scans Kubernetes clusters for security weaknesses and vulnerabilities.
- kube-hunter-operator: An operator to automate kube-hunter scanning on Kubernetes clusters.
Secrets Management:
- Kubernetes Secrets: Built-in Kubernetes functionality for storing and managing secrets.
- HashiCorp Vault: A popular tool for managing secrets and sensitive data in Kubernetes.
- CyberArk Conjur: Provides secrets management and rotation for Kubernetes environments.
- Identity and Access Management:
Open Policy Agent (OPA): Enables fine-grained authorization and access control for Kubernetes.
- Keycloak: An open-source identity and access management solution that can be integrated with Kubernetes.
- Dex: A federated OpenID Connect provider that allows you to connect Kubernetes with various identity providers.
Runtime Threat Detection and Prevention:
- Sysdig Falco: Monitors system calls and detects abnormal activity or malicious behavior in real-time.
- Aqua Security: Provides runtime protection and anomaly detection for containers and Kubernetes workloads.
- StackRox Kubernetes Security Platform: Offers runtime threat detection and policy enforcement for Kubernetes.
Cloud-Native Security Platforms:
- Twistlock: Provides container and cloud-native security solutions, including vulnerability management, compliance, and runtime protection.
- Sysdig Secure: Offers a comprehensive cloud-native security platform for monitoring, threat detection, and incident response.
- Prisma Cloud: Delivers cloud-native security posture management, compliance, and runtime protection for Kubernetes and other cloud platforms.