Securing Kubernetes clusters is crucial to protect sensitive data, prevent unauthorized access, and ensure the stability and integrity of your applications. Here’s a comprehensive checklist for Kubernetes security:
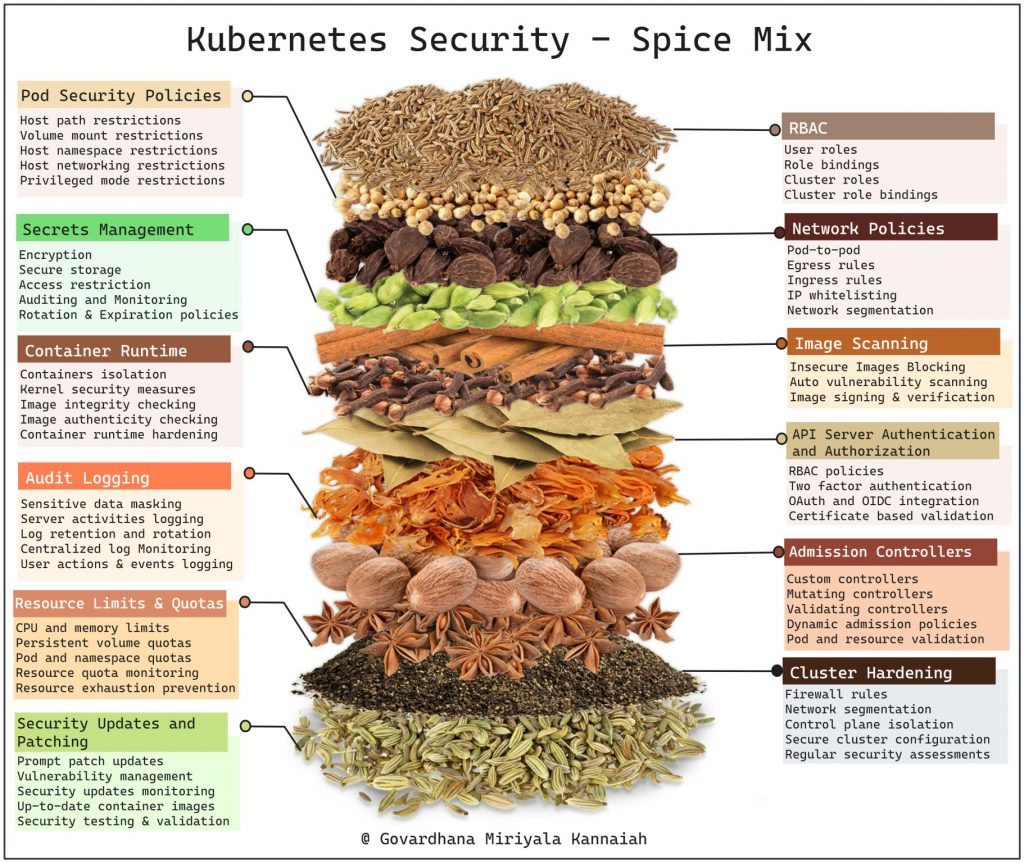
Cluster configuration security:
- Disable or tightly control insecure APIs and features.
- Enable RBAC (Role-Based Access Control) and assign appropriate roles to users and service accounts.
- Restrict access to the Kubernetes API server.
- Use strong authentication mechanisms such as client certificates or token-based authentication.
- Regularly review and update cluster configurations to align with security best practices.
Network security:
- Isolate the Kubernetes cluster from other networks and enforce network segmentation.
- Implement network policies to control traffic between pods and namespaces.
- Utilize network security tools like network firewalls, VPNs, or network policies offered by cloud providers.
- Enable encryption for data in transit using TLS/SSL certificates.
- Use secure communication channels for inter-node communication.
Node security:
- Regularly patch and update the host operating system.
- Isolate nodes in a separate network or subnet.
- Apply security hardening measures to nodes such as disabling unnecessary services, limiting access, and – enabling firewall rules.
- Implement container runtime security mechanisms like AppArmor or SELinux.
- Scan container images for vulnerabilities before deploying them.
Pod security:
- Utilize Kubernetes Pod Security Policies (PSP) to enforce security policies on pods.
- Use the principle of least privilege to assign appropriate access permissions to pods and containers.
- Enable container runtime security features such as resource isolation, namespace restrictions, and read-only file systems.
- Regularly monitor and audit the behavior of pods and containers.
Image security:
- Utilize container registries with built-in security features.
- Scan container images for vulnerabilities and malware.
- Use trusted base images from official repositories.
- Regularly update and patch container images to include the latest security fixes.
Secrets management:
- Avoid hardcoding sensitive information in configuration files or Dockerfiles.
- Store secrets like API keys, passwords, or tokens in Kubernetes Secrets and restrict access to them.
- Encrypt and secure secrets at rest and in transit.
- Regularly rotate secrets and revoke access when necessary.
Logging and monitoring:
- Enable and configure logging for the Kubernetes cluster.
- Implement centralized log management and analysis.
- Monitor for suspicious activities, unauthorized access attempts, or security incidents.
- Set up alerts and notifications for security-related events.
- Regularly review and analyze logs to detect and respond to security threats.
Backup and disaster recovery:
- Implement regular backups of critical data and configurations.
- Test the restoration process periodically.
- Define a disaster recovery plan to handle potential security incidents or system failures.
- Store backups in a secure location separate from the production environment.
Security testing and audits:
- Perform regular security assessments and penetration testing.
- Conduct vulnerability scans and security audits.
- Address identified vulnerabilities and weaknesses promptly.
- Follow security best practices and guidelines from Kubernetes and cloud providers.
Education and training:
- Provide security awareness training to developers, administrators, and users.
- Promote a security-conscious culture and ensure that everyone understands their responsibilities.
- Stay updated with the latest security threats, patches, and best practices in the Kubernetes ecosystem.