-

How to do git clone without installing git in WSL (Windows Subsystem for Linux)
In this Article i m going to share the step by step guide to git clone in Windows Subsystem for…
-
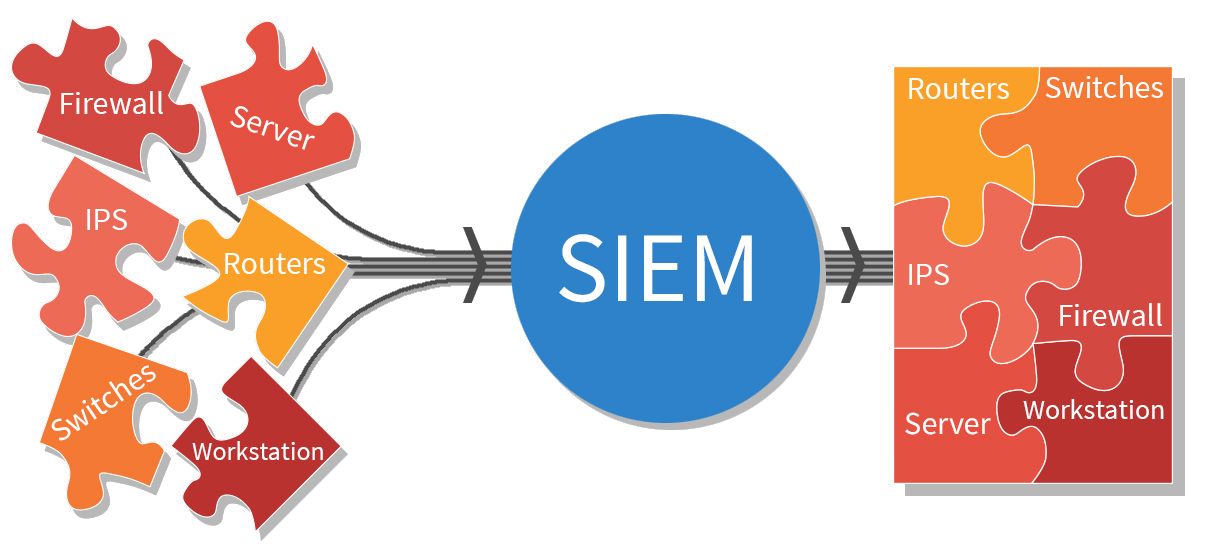
What is Security Information and Event Management (SIEM) Tools?
Combining security information management (SIM) and security event management (SEM) activities into a single security management system is known as…
-
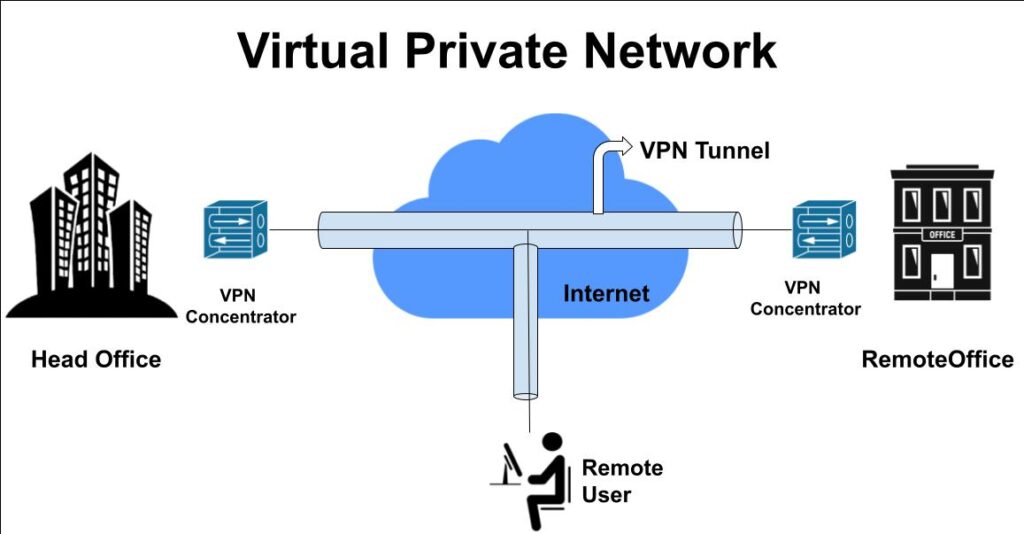
What is Virtual Private Networks (VPNs)?
The virtual private network is known as a VPN. Technology known as a virtual private network (VPN) establishes a secure,…
-

What is Antivirus and Antimalware Software?
Cybersecurity should be prioritized in all enterprises, large and small. If your company’s data gets hacked, the repercussions might be…
-
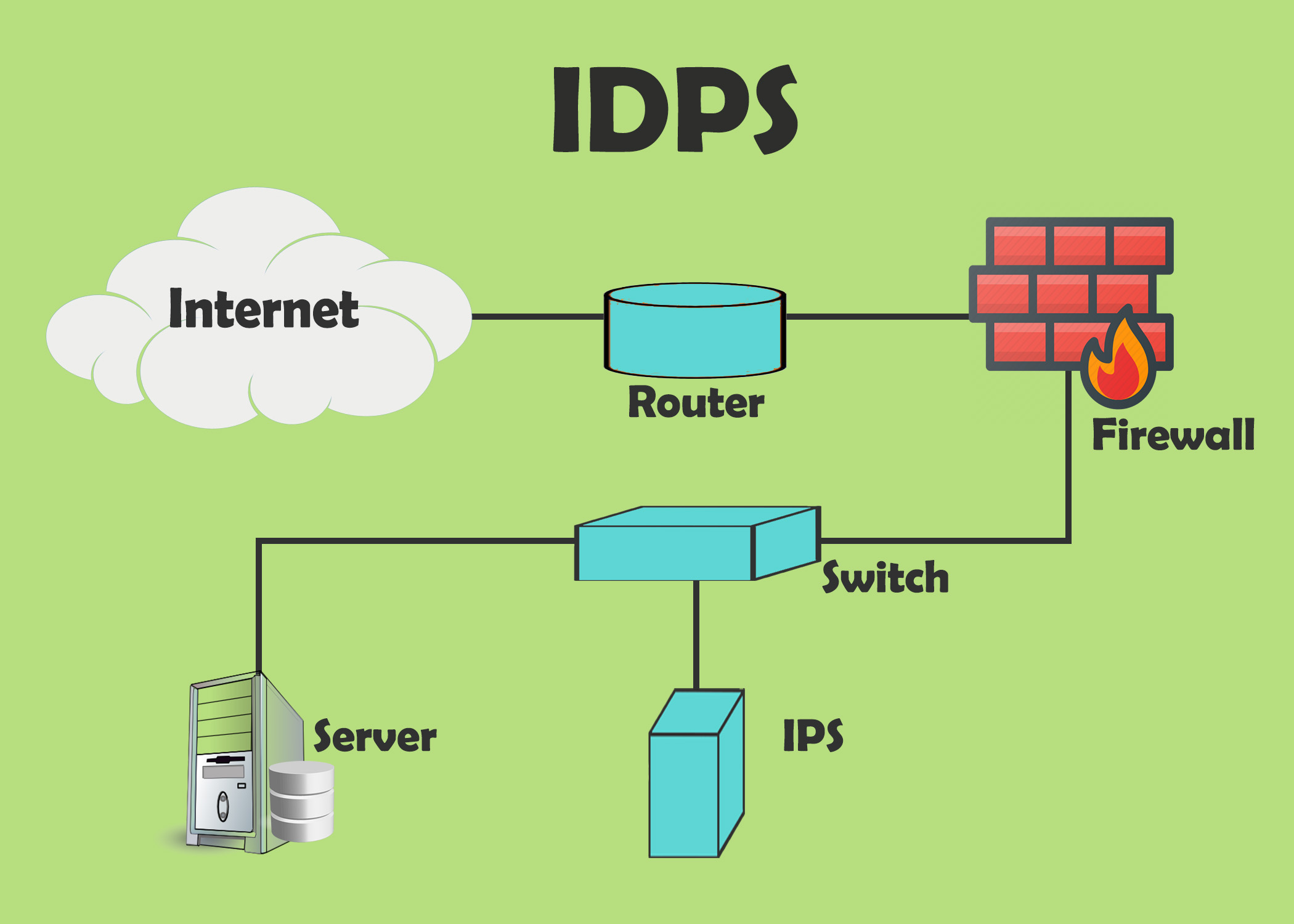
What is Intrusion Detection and Prevention Systems (IDPS)?
Security tools or software known as intrusion detection and prevention systems (IDPS) keep an eye on network traffic and systems…
-
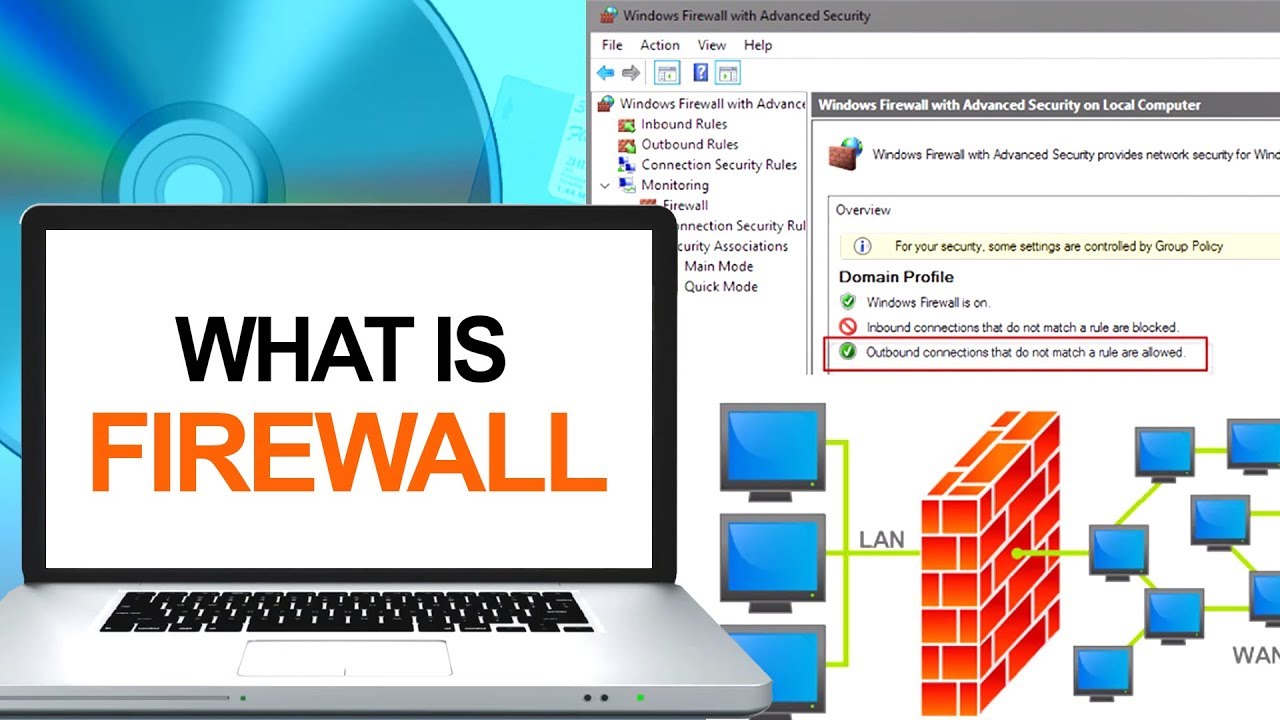
What is Firewalls?
A firewall is a type of network security device that keeps an eye on all incoming and outgoing network traffic…
-
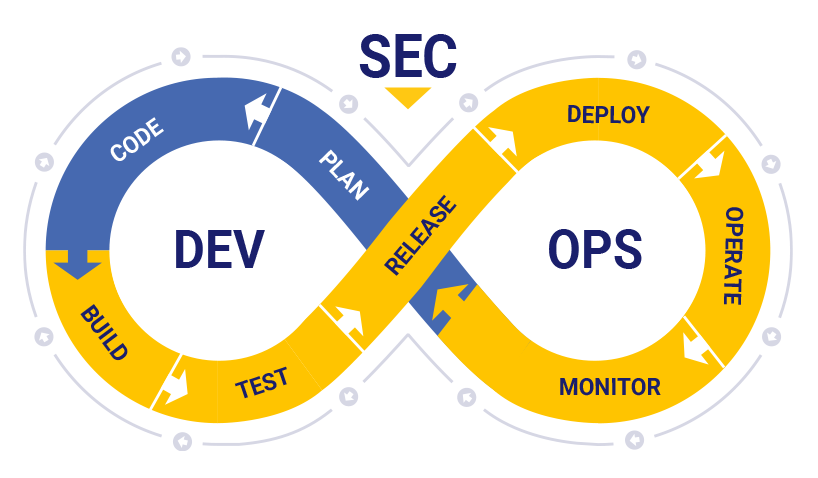
What is DevSecOps? Why? How?
Introduction DevSecOps is a set of practices that aims to integrate security (Sec) into the DevOps process. DevOps is a…
-
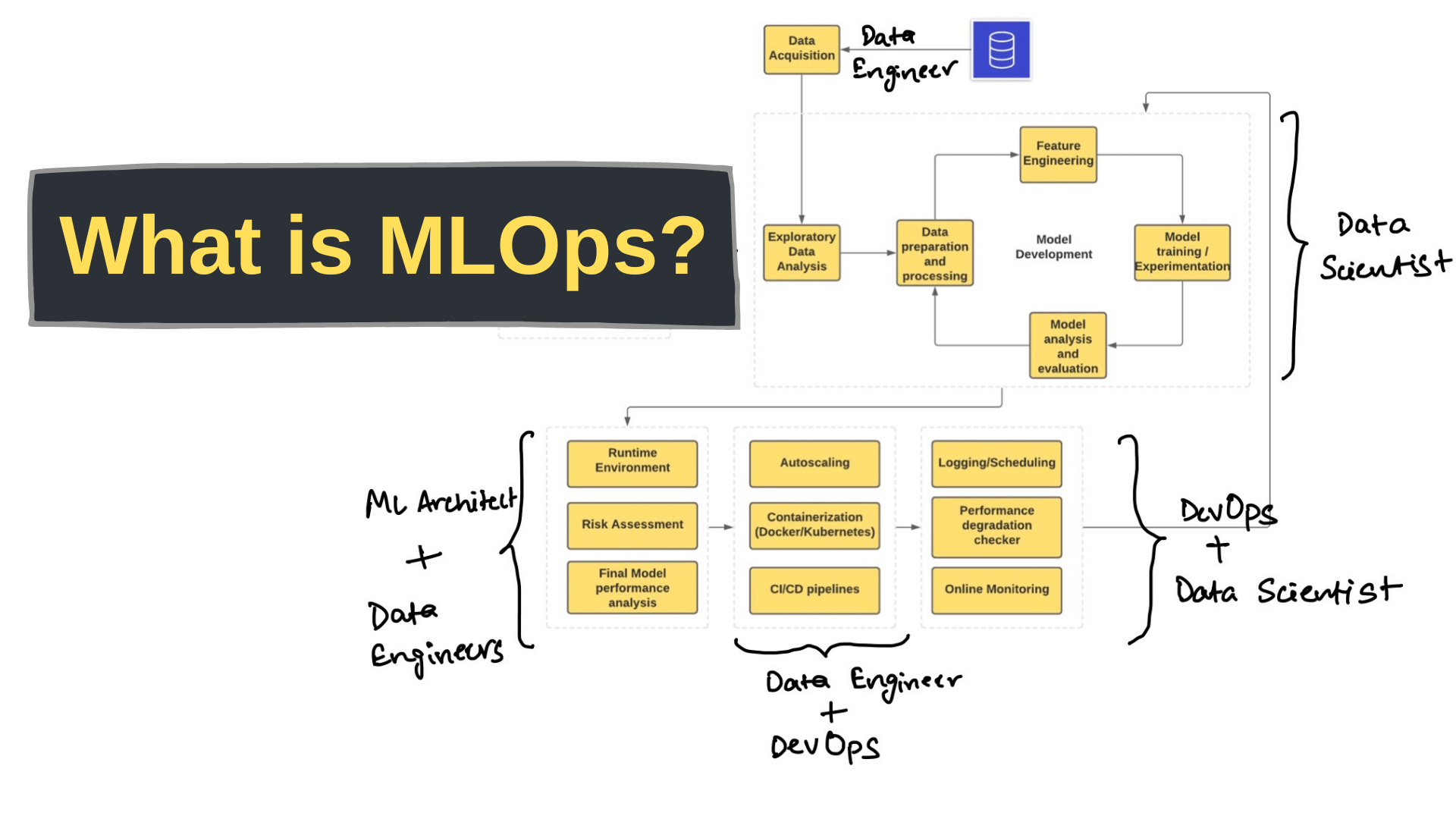
What is mlops? Why? How?
Introduction MLOps, short for Machine Learning Operations, is a set of practices and principles aimed at streamlining and automating the…
-
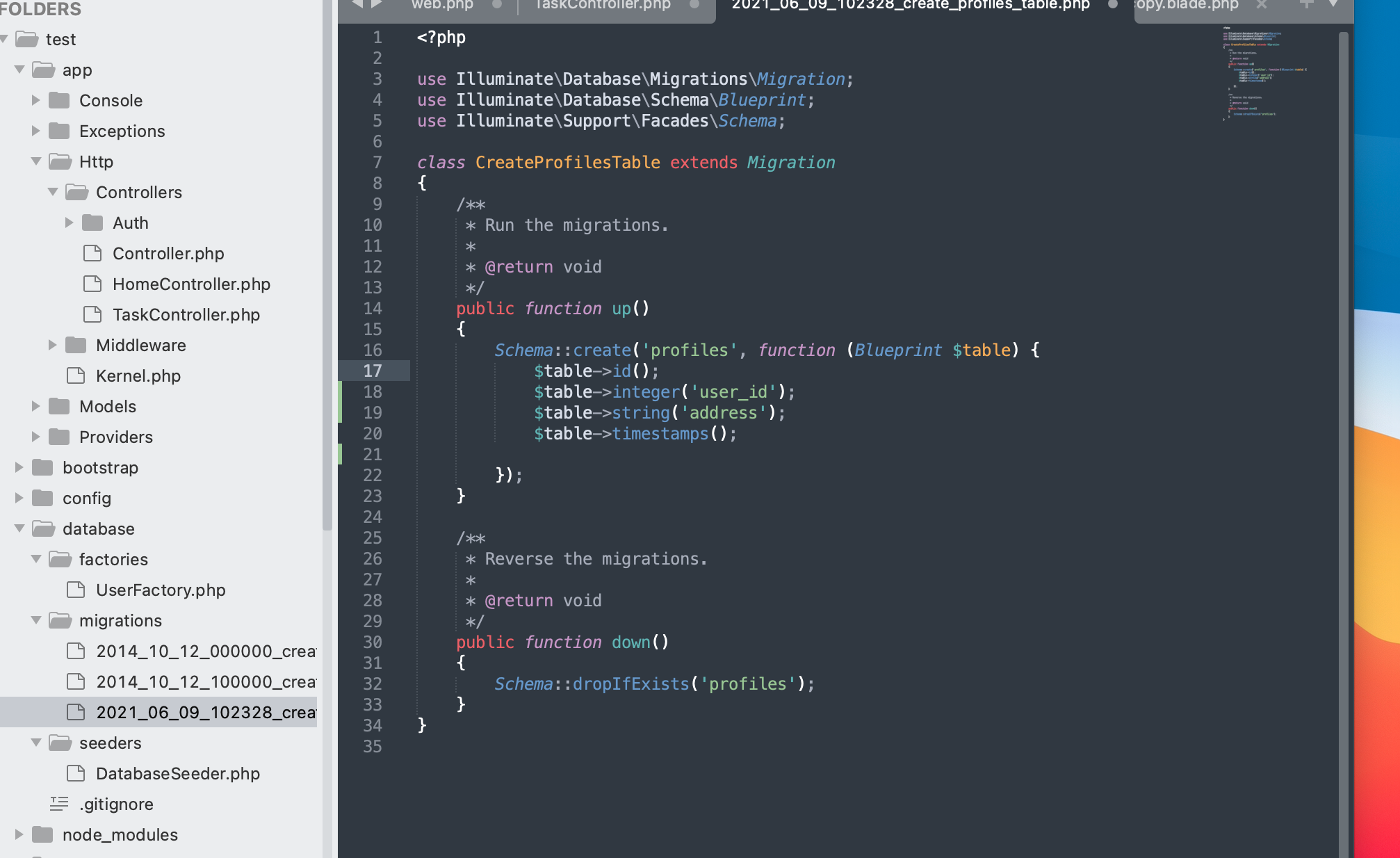
@return void Why this command is used in laravel model project?
In Laravel, the @return void comment is used in PHPDoc-style comments to indicate the return type of a method in…
-
What is aiops? Why & How?
Introduction AIOps, short for Artificial Intelligence for IT Operations, represents a transformative approach to managing and optimizing modern IT infrastructures….
