Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
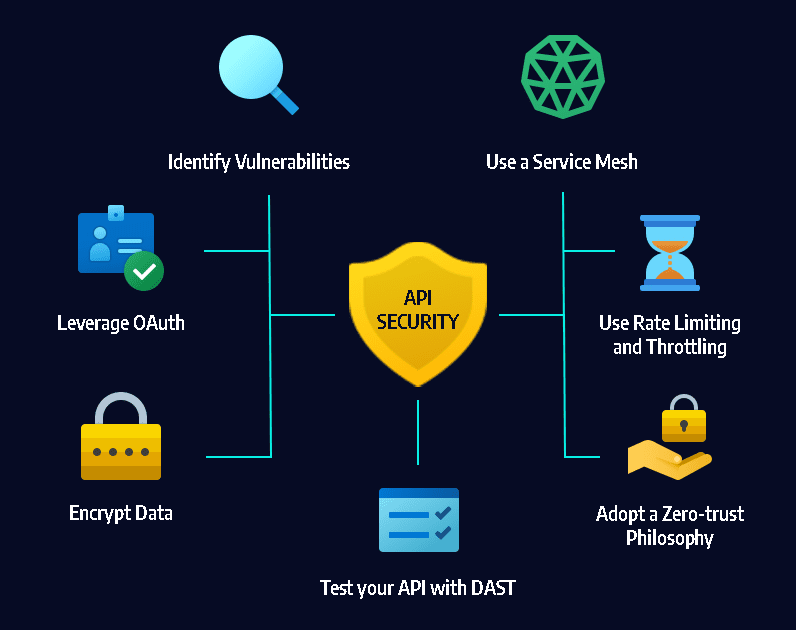
Let’s break down API security further, moving from foundational principles into specific mechanisms, vulnerabilities, and protections. This will help you see not just what is done, but why and how each practice impacts the overall security of your APIs.
1. Authentication & Authorization
- Authentication means verifying who is making the API request. Example methods: API keys, JWT tokens, OAuth2, OpenID Connect.
- API keys: Simple, but mainly identify the calling app or user. Not very secure by themselves.
- JWT/OAuth2: Tokens carry verified identity, expiration times, and claims. Use when you need strong security for modern APIs.
- Authorization controls what actions an authenticated user is allowed to do (permissions). Enforce least privilege everywhere—give the lowest level of access that still lets users do their jobs.
- Best practices:
- Never rely only on simple keys—use strong token-based authentication for sensitive APIs.
- Validate tokens on every request.
- Use HTTPS so tokens and credentials aren’t exposed during transport.
2. Data Encryption & Privacy
- Data must be encrypted both “in transit” (going over the network) and “at rest” (when saved on disk).
- Use TLS (HTTPS) for all API endpoints.
- For stored data, use encryption technologies like AES for databases.
- Why it matters: Without encryption, attackers can “sniff” data on the network or steal files from servers and read sensitive information, even if they can’t log in.
- Watch out for: Logging or caching mechanisms accidentally storing sensitive data unencrypted.
3. API Gateway & Traffic Management
- API gateways act as a protection layer: they can enforce authentication, rate limits, logging, and monitor for threats.
- Rate limiting (explained earlier) is often enforced here—protecting your backend from misuse or traffic spikes.
- Static vs dynamic rate limiting:
- Static: Same limit for everyone (e.g., 1000 req/hour per user).
- Dynamic: Adjusts based on user reputation or past patterns. Better at catching sudden attacks.
4. Input Validation & Threat Prevention
- Never trust user input—even if it comes through your API from a mobile or web app you built yourself.
- SQL Injection: Happens when attackers trick your server into running their own database commands. Prevented with parameterized queries (prepared statements) and strict input checking.
- Input sanitization: Remove unexpected or dangerous characters/commands before processing.
- Schema enforcement: Use tools that only accept input matching exactly your expected data structure.
5. Common Attack Vectors Explained
a. Cross-Origin Resource Sharing (CORS)
- Protects against web browsers making unauthorized cross-domain requests via frontend code. If you’re building browser-based apps, configure CORS to only allow requests from trusted origins.
- Never use
*(wildcard) in CORS in production—it means “anyone can access my API”.
b. CSRF (Cross-Site Request Forgery)
- Trick: Causes a user’s browser (where they’re logged in) to submit malicious requests to your API without them knowing.
- Prevent with unique CSRF tokens in forms/headers and by making APIs require tokens for any action that changes state.
- Note: APIs using ONLY tokens (e.g., JWT in headers, no cookies) are less exposed to CSRF, but beware if users can authenticate via cookies.
c. XSS (Cross-Site Scripting)
- Malicious script gets injected somewhere (like a comment field) and executed in a user’s browser.
- For API developers: Always sanitize any data that may later be shown in a browser—ensure your frontend escapes HTML/JavaScript to prevent this.
6. Advanced Modern Security Concepts
- Zero Trust Architecture: Always verify every request, treat all network traffic as hostile unless proven otherwise.
- Continuous Testing: Use tools like Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and penetration testing as part of your build pipeline. Regularly scan for vulnerabilities.
- Logging & Monitoring: Log every critical action and access attempt—even failed ones. Use automated tools to flag unusual patterns (like many failed logins, or data access outside business hours).
- Incident Response: Have a written plan for what happens if someone discovers a security issue or breach—know how to quarantine systems, notify stakeholders, and patch vulnerabilities quickly.
7. Summary & Mindset Shift
API security isn’t a “set-and-forget” checklist; it’s a mindset of constant vigilance. Key habits include:
- Questioning default settings and permissions.
- Automating and reviewing security tests.
- Revisiting your controls as your API and its use cases grow or change.

Leave a Reply