Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
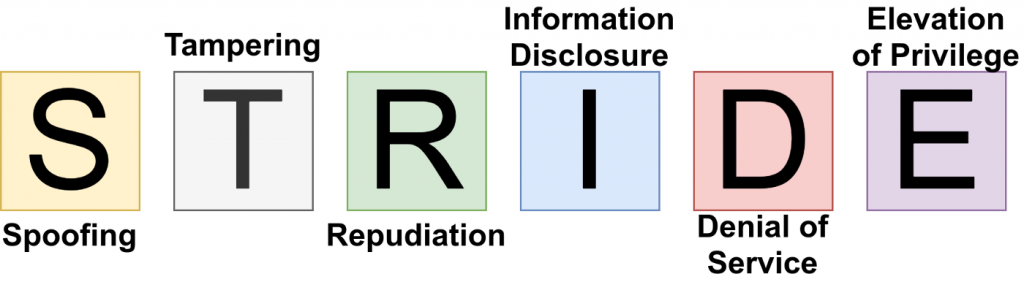
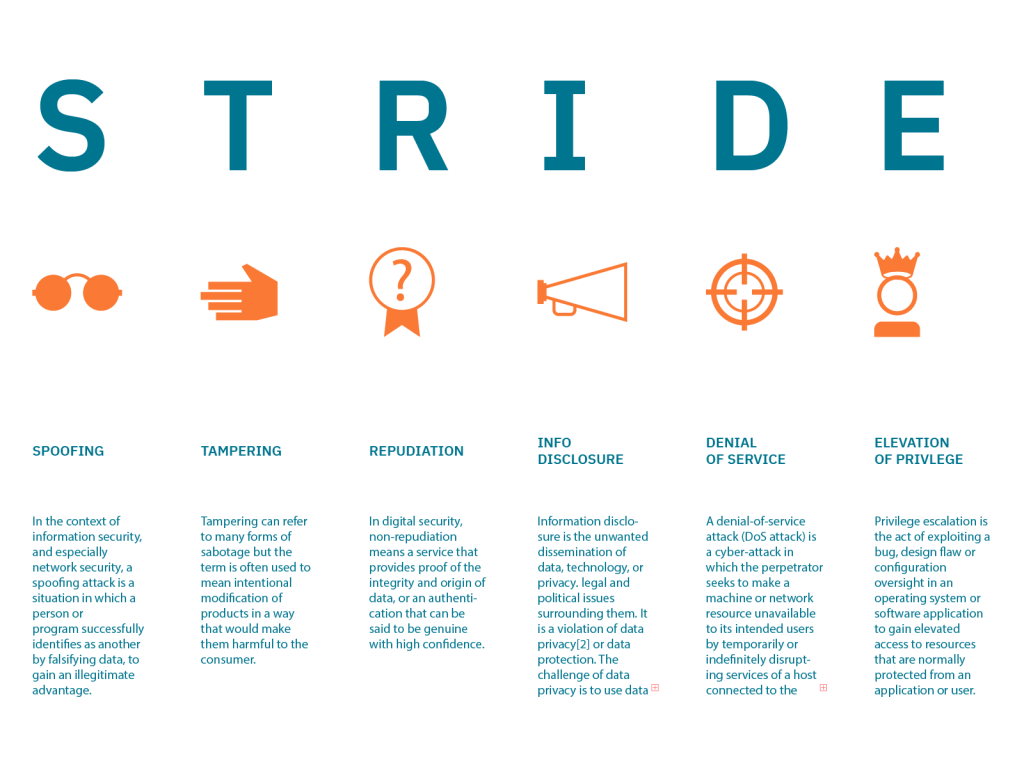
STRIDE is an acronym that stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. It is a threat modeling framework used to identify and evaluate potential security threats to a system or application.
The acronym STRIDE represents the following threat categories:
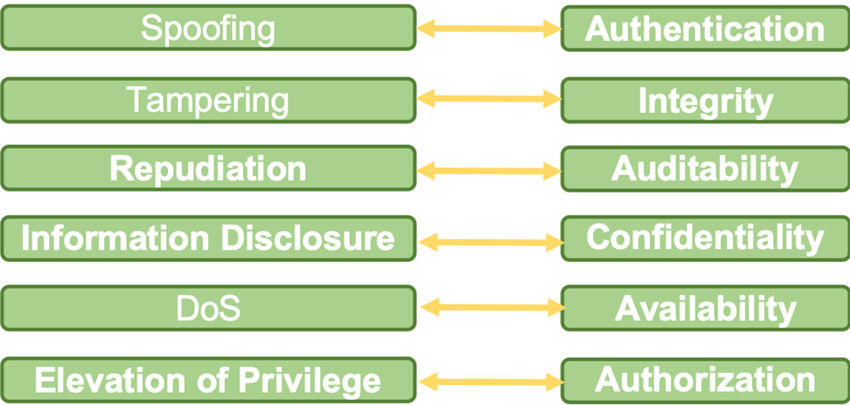
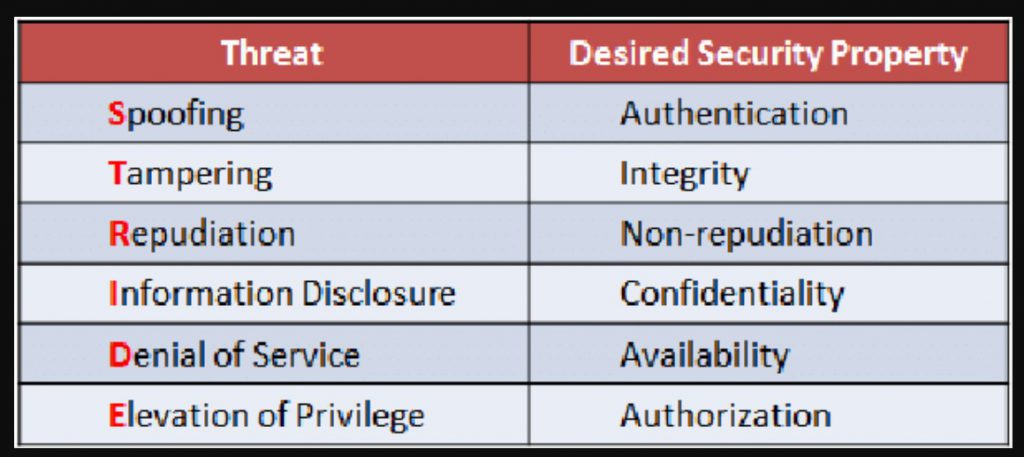
- Spoofing: Impersonating a legitimate user or system to gain access to resources or information.
- Tampering: Modifying or altering data or system configurations.
- Repudiation: Denying that an action was taken or that a transaction occurred.
- Information Disclosure: Unauthorized access to or disclosure of sensitive information.
- Denial of Service: Disrupting the availability of a system or service.
- Elevation of Privilege: Gaining access to resources or privileges that a user should not have.
STRIDE can be used to identify potential threats and vulnerabilities, and to develop strategies to mitigate or prevent them. It is often used in the software development process, to ensure that security is considered throughout the development cycle.
Benefits of STRIDE?
STRIDE is a useful tool for identifying and evaluating potential security threats to a system or application. The benefits of using the STRIDE framework include:
- Systematic approach: STRIDE provides a systematic approach for identifying and evaluating potential security threats, which can help to ensure that all potential threats are considered.
Prioritization: By categorizing threats into specific categories, such as spoofing, tampering, and elevation of privilege, it allows to prioritize the threats that are most likely to occur and have the greatest impact. - Risk assessment: By identifying and evaluating potential threats, STRIDE can help to assess the risk associated with those threats and to develop strategies to mitigate or prevent them.
- Communication: STRIDE can be used to communicate security risks and concerns to stakeholders, and to involve them in the threat modeling process.
- Continuous improvement: By regularly reviewing and updating the threat model, STRIDE can help to ensure that security is continually improved over time.
STRIDE can also be used in conjunction with other threat modeling frameworks such as PASTA (Process for Attack Simulation and Threat Analysis) and Trike to identify security threats and improve the security of your systems and applications.
Overall, the use of STRIDE framework can help organization to achieve better security posture and reduce the attack surface.
How to implement STRIDE?

Implementing the STRIDE framework involves several steps:
- Identify assets: Identify the assets that need to be protected, such as data, systems, and networks.
- Identify threat actors: Identify the potential threat actors, such as internal employees, external attackers, or malicious insiders.
- Identify threats: Use the STRIDE categories to identify potential threats that might affect the assets. For example, consider how an attacker might try to spoof a user identity, tamper with data, or perform a denial-of-service attack.
- Evaluate risks: Evaluate the risks associated with each identified threat by considering the likelihood of the threat occurring and the impact if it does occur.
- Develop mitigation strategies: Develop strategies to mitigate or prevent the identified threats. These might include technical controls, such as firewalls or intrusion detection systems, as well as operational controls, such as security policies or employee training.
- Implementation: Implement the mitigation strategies and controls to reduce the risk of the identified threats.
- Monitoring: Regularly monitor and review the system to ensure that the controls are functioning as intended and that new threats have not emerged.
- Continuous Improvement: Continuously improve the security posture by reviewing the threat model and updating it as needed.
It’s important to involve all stakeholders in the process





