Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
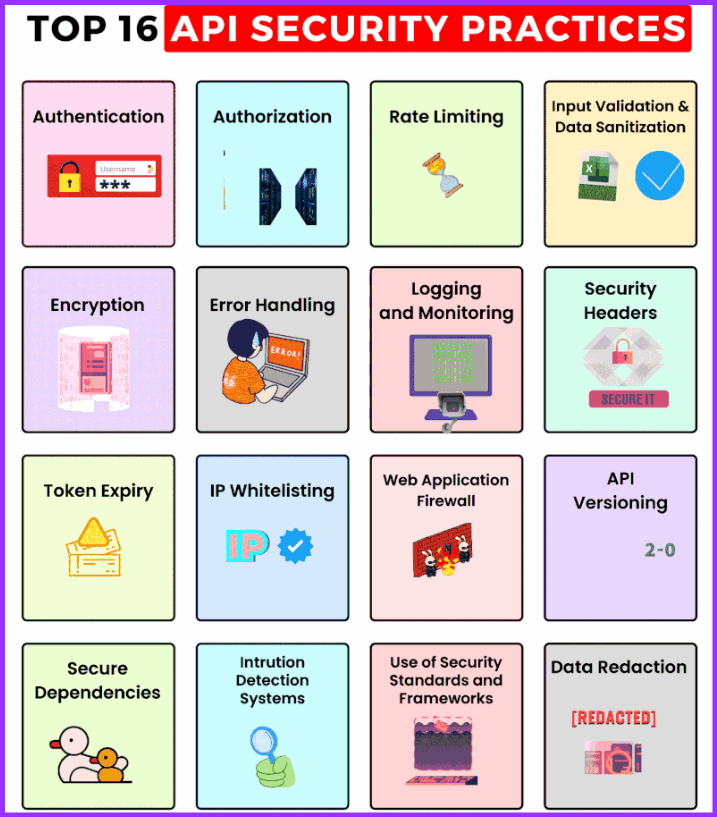
API security is of paramount importance to protect sensitive data and maintain the integrity of systems. Here are some top API security practices:
- Authentication and Authorization: Implement strong authentication mechanisms to ensure that only authorized users or applications can access your API. Use OAuth, API keys, or JWT (JSON Web Tokens) for secure authentication and authorization.
- Use HTTPS: Always use HTTPS (TLS/SSL) for transmitting data between clients and the API server. HTTPS encrypts data during transmission, preventing eavesdropping and man-in-the-middle attacks.
- Input Validation and Sanitization: Validate and sanitize all incoming data to prevent injection attacks (e.g., SQL injection, XSS). Use parameterized queries and avoid executing user-supplied data in commands.
- Output Encoding: Encode API responses correctly to prevent script injection attacks (XSS). Use content type negotiation to ensure the proper response format is returned.
- Rate Limiting and Throttling: Implement rate limiting and request throttling to prevent abuse and protect against DDoS attacks.
- Avoid Sensitive Data in URLs: Avoid passing sensitive data (e.g., passwords, tokens) in URLs, as they may get logged in various systems.
- JWT Best Practices: If using JWT for authentication, follow best practices such as setting a reasonable expiration time, not storing sensitive information in the token, and using strong cryptographic algorithms.
- Least Privilege Principle: Grant the least privilege required for users or applications accessing the API. Limit access to only the necessary resources and actions.
- Secure Error Handling: Avoid displaying sensitive information in error messages. Provide generic error messages to end-users and log detailed errors for debugging purposes.
- API Versioning: Use versioning to manage changes in the API and avoid breaking existing client applications.
- Audit and Monitor API Activity: Implement logging and monitoring mechanisms to track API usage and detect suspicious activities or anomalies.
- Regularly Update and Patch: Keep the API server, libraries, and dependencies up-to-date with the latest security patches to mitigate known vulnerabilities.
- Secure Data Transmission and Storage: Encrypt sensitive data both in transit and at rest. Use strong encryption algorithms and ensure proper key management.
- Implement Two-Factor Authentication (2FA): For highly sensitive APIs, consider adding an extra layer of security with two-factor authentication to ensure stronger user verification.
- Security Testing: Regularly conduct security assessments, penetration testing, and code reviews to identify and address potential security vulnerabilities.
- API Gateway: Consider using an API gateway to centralize security policies, handle authentication, and manage traffic to backend services.
- Security Headers: Set appropriate security headers in API responses to protect against common web vulnerabilities.
- Implement authentication and authorization. This is the most basic level of API security, and it ensures that only authorized users can access your APIs. There are a number of different authentication methods available, such as OAuth 2.0, API keys, and username/password.
- Use SSL/TLS encryption. This encrypts all traffic between your APIs and clients, making it much more difficult for attackers to intercept and steal data.
- Implement rate limiting. This limits the number of requests that a client can make to your APIs in a given period of time. This can help to protect your APIs from denial-of-service attacks.
- Use auditing and logging. This helps you to track all API activity, so that you can identify any suspicious or malicious behavior.
- Restrict access to sensitive data. Only allow authorized users to access sensitive data, such as passwords, credit card numbers, and social security numbers.
- Use a security gateway. A security gateway can help to protect your APIs from a variety of threats, such as cross-site scripting (XSS) attacks, SQL injection attacks, and denial-of-service attacks.
- Keep your APIs up to date. Software updates often include security patches, so it’s important to keep your APIs up to date to protect them from known vulnerabilities.
In addition to these general practices, there are a number of specific security measures that you can take to protect your APIs, depending on the specific type of API you are developing. For example, if you are developing a REST API, you should consider using the following security measures:
Use JSON Web Tokens (JWTs) for authentication and authorization. JWTs are a secure way to transmit authentication and authorization information between your APIs and clients.
Use HTTPS for all API requests and responses. This ensures that all traffic between your APIs and clients is encrypted.
Validate all API input data. This helps to protect your APIs from malicious input that could be used to exploit vulnerabilities.
Use API versioning. This helps to protect your APIs from breaking changes that could be introduced in new versions.





