Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
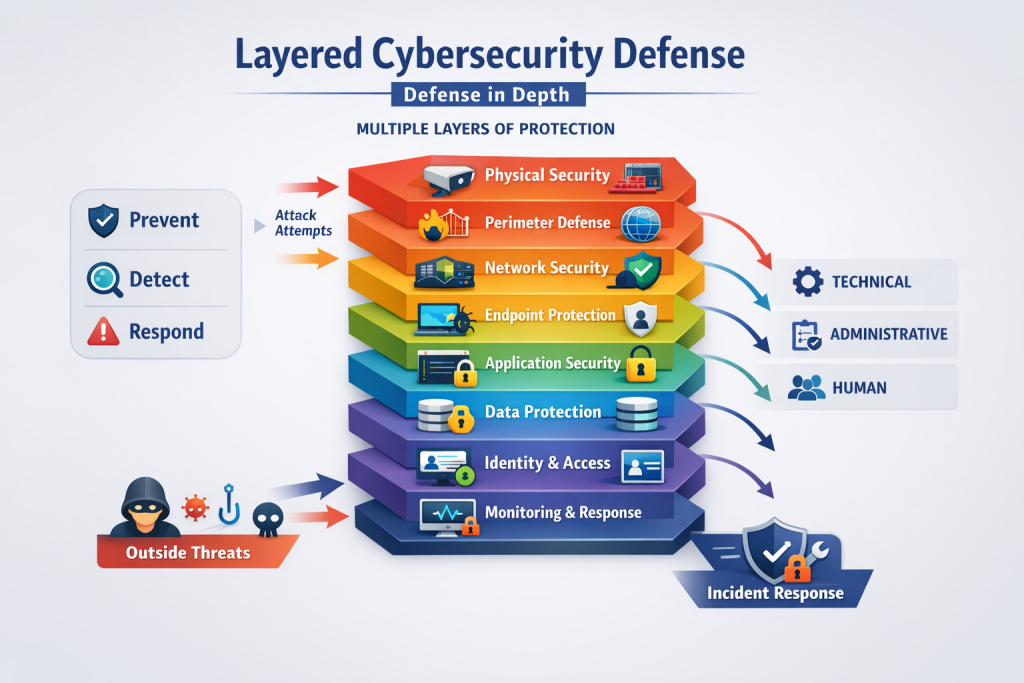
Layering in cybersecurity—commonly known as Defense in Depth—is a security strategy where multiple security controls are placed at different levels of an IT system to protect against cyber threats. Instead of relying on a single security tool or control, organizations build overlapping layers of defense so that if one layer fails, another layer continues to provide protection.
Modern cyberattacks are rarely simple. Attackers use phishing, malware, stolen credentials, misconfigurations, and insider techniques—often in combination. Because of this, no single security solution is enough. Layering ensures that attacks are slowed down, detected early, and contained before they cause serious damage.
In today’s environments—cloud, mobile, DevOps, APIs, and remote work—layered security is no longer optional. It is a foundational principle of effective cybersecurity architecture.
Why Layering Is Essential in Modern Cybersecurity
Cybersecurity threats have evolved dramatically:
- Attacks are automated and scalable
- Zero-day vulnerabilities exist
- Credentials are frequently leaked
- Insider threats are real
- Systems are highly interconnected
Relying on one security control creates a single point of failure. Layering removes that weakness by ensuring:
- Failures do not result in full compromise
- Attacks are detected at multiple stages
- Damage is limited even after a breach
Layered security aligns with real-world conditions where breaches are assumed to happen, and systems are designed to survive them.
Core Concept: Defense in Depth Explained
Defense in Depth means applying security controls across three dimensions:
- People – users, administrators, training, awareness
- Processes – policies, procedures, incident response
- Technology – tools, platforms, and security systems
The idea is not perfection at one layer, but resilience across many layers.
High-Level View of a Layered Cybersecurity Architecture

Each layer protects against different threat types and attack stages.
Layer 1: Physical Security
What This Layer Protects
Physical security protects the actual hardware that stores and processes data.
Key Components
- Secure data centers
- Access cards, biometrics
- Surveillance systems
- Locked server racks
- Environmental controls
Why It Matters
If an attacker gains physical access, many digital controls can be bypassed entirely. Physical security is the foundation of all other layers.
Layer 2: Perimeter Security
Purpose
Controls what enters and exits the organization’s network.
Key Controls
- Network firewalls
- Web Application Firewalls (WAF)
- VPN gateways
- DDoS protection
Threats Addressed
- External intrusion attempts
- Automated scanning attacks
- Unauthorized network access
Perimeter security acts as the first digital barrier, filtering obvious threats before they reach internal systems.
Layer 3: Network Security
Purpose
Protects internal network traffic and prevents lateral movement.
Key Controls
- Network segmentation
- Intrusion Detection Systems (IDS)
- Intrusion Prevention Systems (IPS)
- Secure routing and switching
- Zero Trust networking principles
Why This Layer Is Critical
Many breaches fail not at entry, but because attackers move freely inside the network. Network security limits blast radius.
Layer 4: Endpoint Security
Purpose
Protects devices used by employees and systems.
Examples
- Antivirus and anti-malware
- Endpoint Detection and Response (EDR)
- Device encryption
- OS and software patching
Threats Addressed
- Malware
- Ransomware
- Trojans
- Unauthorized software
Endpoints are the most common attack surface, especially with remote work.
Layer 5: Application Security
Purpose
Protects applications from being exploited.
Key Practices
- Secure coding standards
- Input validation
- Authentication checks
- Rate limiting
- Application-level firewalls
Common Attacks Prevented
- SQL injection
- Cross-site scripting (XSS)
- Broken authentication
- API abuse
Most modern attacks target applications, not infrastructure. This layer is essential for web and mobile platforms.
Layer 6: Data Security
Purpose
Protects sensitive information regardless of where it resides.
Controls
- Encryption at rest and in transit
- Data classification
- Backup and recovery
- Data Loss Prevention (DLP)
Why This Layer Matters
Even if attackers access systems, data security ensures information remains unusable or traceable.
Layer 7: Identity and Access Management (IAM)
Purpose
Ensures only authorized users access systems and data.
Key Controls
- Multi-Factor Authentication (MFA)
- Role-Based Access Control (RBAC)
- Least privilege access
- Single Sign-On (SSO)
Threats Addressed
- Credential theft
- Account takeover
- Privilege escalation
Identity is now the primary security boundary in cloud and SaaS environments.
Layer 8: Monitoring, Logging, and Detection
Purpose
Detects suspicious activity and security incidents.
Key Tools
- Centralized logging
- Security Information and Event Management (SIEM)
- Behavioral analytics
- Alerting systems
Why Detection Is a Layer
Prevention alone is not enough. Detection ensures that silent failures are noticed quickly.
Layer 9: Incident Response and Recovery
Purpose
Minimizes damage after a security incident.
Core Elements
- Incident response plans
- Isolation procedures
- Backup restoration
- Post-incident analysis
A layered defense assumes incidents will occur and focuses on rapid containment and recovery.
Layer 10: Human and Policy Layer
Purpose
Addresses human behavior, governance, and compliance.
Components
- Security awareness training
- Clear policies and procedures
- Access reviews
- Compliance audits
Many attacks succeed due to human error, not technical failure. This layer closes that gap.
How Layering Works in a Real Attack Scenario
Example: Phishing Attack
- Phishing email bypasses spam filter
- User clicks malicious link
- MFA prevents account takeover
- Endpoint security detects payload
- Network monitoring flags anomaly
- Incident response isolates the device
Each layer plays a role. The attack fails not because one control worked perfectly, but because multiple controls worked together.
Layering vs Single-Layer Security
| Aspect | Single-Layer Security | Layered Security |
|---|---|---|
| Failure impact | Total compromise | Limited damage |
| Detection | Often late | Early and continuous |
| Resilience | Low | High |
| Scalability | Weak | Strong |
| Modern threats | Poor defense | Effective defense |
Layering and Zero Trust: How They Relate
Layering and Zero Trust are complementary, not competing ideas.
- Layering provides multiple defenses
- Zero Trust removes implicit trust
- Together, they create resilient systems
Zero Trust focuses heavily on identity, verification, and segmentation, which fits naturally into a layered model.
Best For: Who Benefits Most from Layered Security?
- Enterprises with complex IT environments
- Cloud-native and SaaS platforms
- Healthcare, finance, and regulated industries
- DevOps and microservices architectures
- Organizations handling sensitive data
Not Ideal For: When Full Layering May Be Excessive
- Very small, low-risk systems
- Short-lived experimental projects
- Isolated, offline environments
Even in these cases, basic layering is still recommended.
Common Mistakes in Implementing Layered Security
- Relying too heavily on tools instead of processes
- Poor integration between layers
- No monitoring or logging
- Ignoring human factors
- Overlapping tools without strategy
Layering must be designed, not randomly assembled.
Best Practices for Building a Layered Defense System
- Start with risk assessment
- Protect identity first
- Encrypt sensitive data everywhere
- Segment networks and services
- Log everything critical
- Test incident response regularly
- Train users continuously
Final Summary
Layering in cybersecurity defense systems is the practice of protecting systems through multiple, coordinated security layers across people, processes, and technology. It recognizes that failures will occur and focuses on resilience, detection, and recovery, not just prevention.
A well-designed layered security architecture does not depend on perfection. It depends on depth, visibility, and coordination—making successful attacks harder, slower, and far less damaging.

Leave a Reply