Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
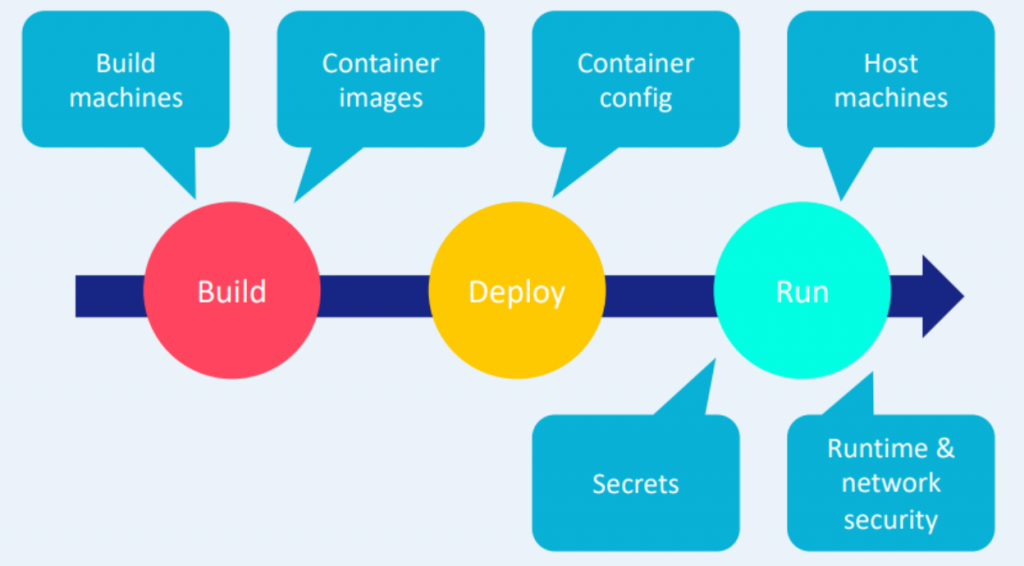
Securing containers is crucial to ensure the integrity and stability of your applications. Here is a detailed process to help you secure containers effectively:
Use Trusted Base Images:
- Start with trusted base images from official repositories or reputable sources.
- Regularly update and patch base images to include the latest security fixes.
- Avoid using outdated or unsupported base images.

Implement Secure Container Image Practices:
- Minimize the attack surface by removing unnecessary packages and dependencies from the container image.
- Only include essential libraries and binaries required by your application.
- Follow the principle of least privilege when setting up user privileges and access controls within the container.
Scan Container Images for Vulnerabilities:
- Utilize container image scanning tools to identify and remediate vulnerabilities.
- Regularly scan container images, both during the development phase and before deployment.
- Integrate vulnerability scanning into your CI/CD pipeline to automate the process.
- Ensure Secure Image Distribution:
Store container images in secure and trusted container registries.
- Implement access controls and authentication mechanisms to restrict access to container images.
- Utilize image signing and verification to ensure the integrity and authenticity of the images.
Container Runtime Security:
- Utilize container runtime security mechanisms provided by the container runtime engine (e.g., Docker, containerd):
- AppArmor or SELinux: Enable mandatory access control policies to restrict container actions.
- Seccomp: Define system call filters to restrict the capabilities of the container.
- Namespaces: Isolate containers by creating separate namespaces for processes, network, and file systems.
- Enable read-only file systems within the container to prevent unauthorized modifications.
- Restrict container resource usage to prevent resource exhaustion attacks.
Secure Container Orchestration:
- Implement proper authentication and authorization mechanisms for container orchestration platforms like Kubernetes:
- Use RBAC (Role-Based Access Control) to assign appropriate permissions to users and service accounts.
- Enable encryption for communication channels within the container orchestration platform.
- Restrict access to the Kubernetes API server and control API server security settings.
Implement Network Segmentation:
- Utilize network policies or firewall rules to control inbound and outbound network traffic for containers.
- Implement container network isolation to prevent unauthorized communication between containers.
Monitor Container Behavior:
- Monitor container activities and behaviors for any abnormal or suspicious activities.
- Leverage container runtime security tools and solutions to detect potential threats and vulnerabilities.
- Implement centralized logging and monitoring solutions to collect container logs and monitor for security events.
Secrets Management:
- Avoid hardcoding sensitive information like passwords, API keys, or tokens in container images.
- Utilize secrets management solutions provided by your container orchestration platform (e.g., Kubernetes Secrets) or external tools (e.g., HashiCorp Vault) to store and manage secrets securely.
- Encrypt and protect secrets at rest and in transit.
Regularly Update and Patch Containers:
- Stay updated with security advisories and patches released by the container runtime engine, base images, and the underlying operating system.
- Establish a process to regularly update and patch containers with the latest security fixes.
Continuous Security Testing and Auditing:
- Perform regular security assessments, penetration testing, and vulnerability scanning for containers.
- Conduct security audits to ensure compliance with security best practices and policies.
- Address identified vulnerabilities and weaknesses promptly.
Education and Training:
- Educate developers and operations teams on container security best practices.
- Provide training on secure container configuration, image scanning, and secure coding practices.