Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
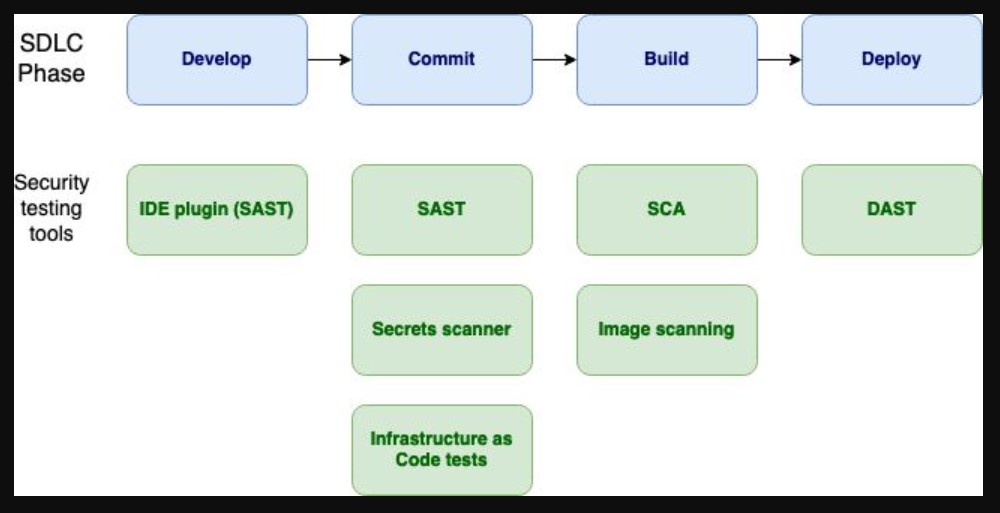
🚀 What is SAST?
🛡️ SAST is a white-box security testing technique which analyzes source code for security vulnerabilities and flaws.
🛡️ It helps developers identify and fix vulnerabilities during the coding phase.
🛡️ SAST can detect security vulnerabilities such as input validation, range errors, API abuse, code quality issues, and any vulnerabilities from the OWASP Top 10 or SANS Top 25.
🛡️ SAST can be automated by integrating it into the DevOps pipeline and executing it repeatedly against check-ins and nightly builds.
🚀 How to use SAST?
🛡️ Identify SAST tool(s) that works for the programming language, framework, or libraries in use. Note that one tool may not fit all in today’s microservices environment as multiple languages/frameworks are used for each microservice.
🛡️ Deploy the SAST tool in the respective development environment by providing access and necessary integration with the CI/CD pipeline and/or IDE.
Note: linting is supported by some SAST tools in the IDE. You may use it for tools consolidation.
🛡️ Run SAST during pre-code check-in, pre-commit, and post-commit. Configure the CI/CD pipeline with phase gates based on the error type to stop or continue. Log and generate issues in the repository.
🛡️ Analyze the SAST results to remove any false positives
🛡️ Perform changes on identified issues as per the recommendation
🚀 Few commendable open source & community edition SAST tools are:
OWASP ZAP, Bandit (Python), Brakeman (Ruby), Checkmarx (Multi-language), Fortify, Sonarqube, Coverity
Note: There may be more which are common in use, and I missed.
Do mention in comments & I will include.





