Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
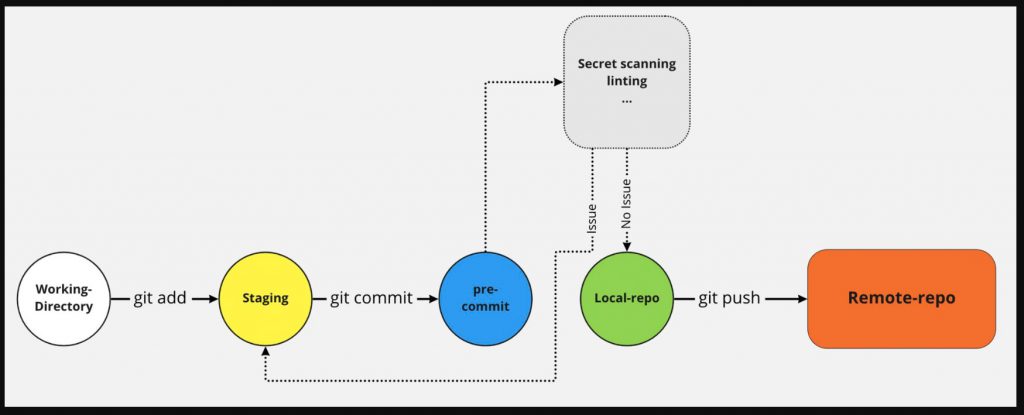
📍 Code lints are the pre-commit hooks in DevSecOps pipeline to automate checking the code for the following:
📌 detect code errors that can lead to a security vulnerabilities
📌 check for “bad code smells” flagging programming errors, bugs, style, and construct errors
📌 suggest code quality improvements
📌 identify unreachable codes
📌 help dereferencing null pointers
📌 help to measure quality & complexity metrics
📌 compare against security focused coding standards
🛡️ Few open-source linting tools
📌 JSLint, JSHint & ESLint: Popular JavaScript linters that can also be used with other languages such as TypeScript.
📌 SonarLint: A static code analysis tool that can be used to perform code analysis, measure technical debt, and detect security vulnerabilities.
📌 Pylint & Flake8: Linters for Python that can help detect errors and improve code quality.
📌 RuboCop: A code linting tool for the Ruby programming language that can help enforce coding conventions and best practices.
📌 Checkstyle: A development tool to help programmers write Java code that adheres to a coding standard for Java
📌 Clang-Tidy: A clang-based C++ linter tool that checks for coding errors and style issues in C++ code.
📌 TFLint & KubeLinter: Linters for Infrastructure as Code. TFLinter used for terraform code reviews & KubeLinter for analyzing K8S Yaml files
🛡️ Benefits of using Code Linters:
📌 Immediate feedback to developers while coding on standard & security vulnerabilities
📌 Improves code quality, accelerates development, reduces time & cost
📌 Results in readable code which makes code understandable & secure
📌 Enforces coding standard including error & exception handling
🛡️ Code Linters challenges:
📌 Different linters for different languages & frameworks
📌 false-positives and information overload for developers





