Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
Quantum computing is on the horizon—no longer the stuff of science fiction, but a rapidly materializing technology that will profoundly disrupt the security ecosystem. Understanding why “quantum-resistant encryption” matters requires grasping both the cryptographic landscape we rely on today and the quantum computer’s unique power.
What Is Post-Quantum Encryption, and Why Is It Needed?
Classical Cryptography and Its Looming Deadline
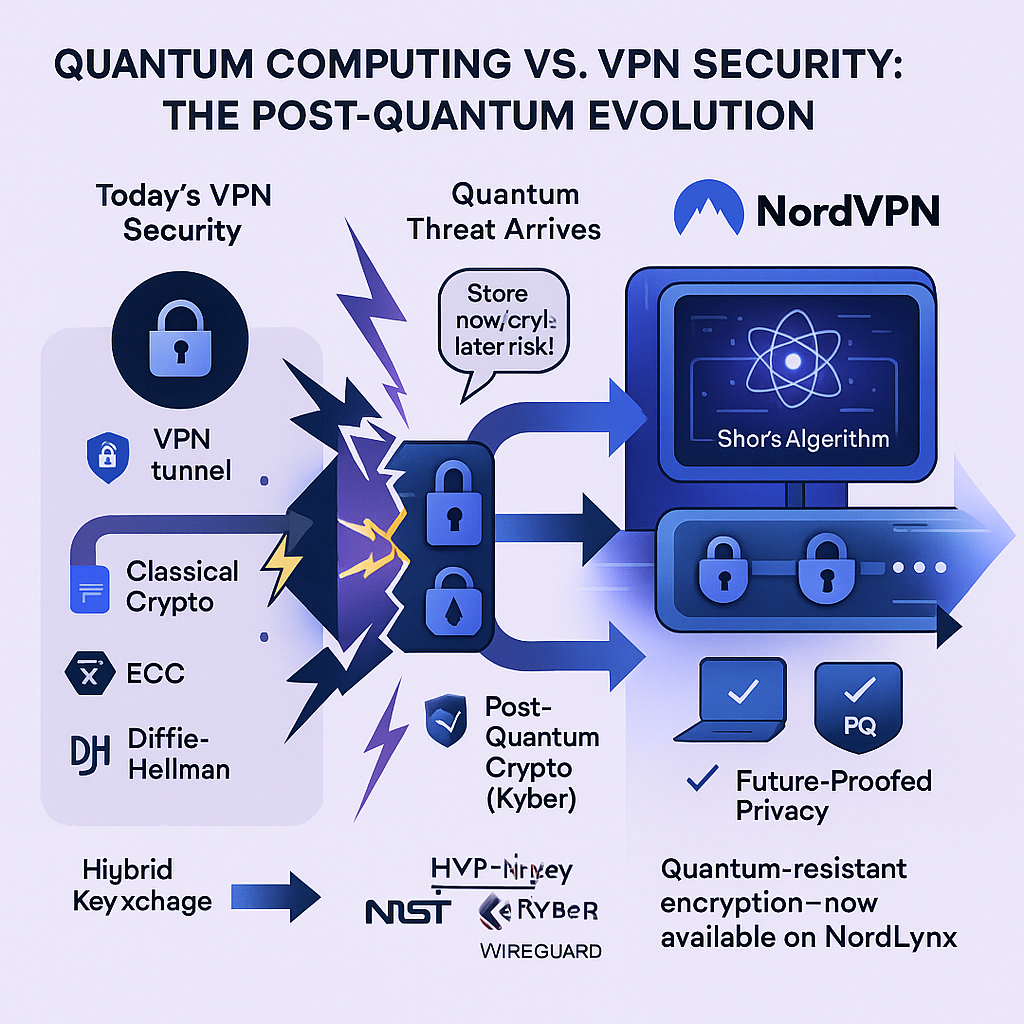
Most of the world’s confidential digital communications, including VPN tunnels, are protected by algorithms like RSA, Diffie-Hellman, and elliptic-curve cryptography (ECC). These rely on mathematical problems—like factoring massive numbers or solving discrete logarithms—that are infeasible for classical supercomputers to crack within any reasonable time frame.
Quantum computers, leveraging the principles of quantum physics, will harness Shor’s algorithm to solve these problems exponentially faster. In practical terms, once large-scale quantum computers are built, they could decrypt traffic that today’s classical encryption deems “unbreakable” in minutes or hours.
Why Does This Matter for VPNs?
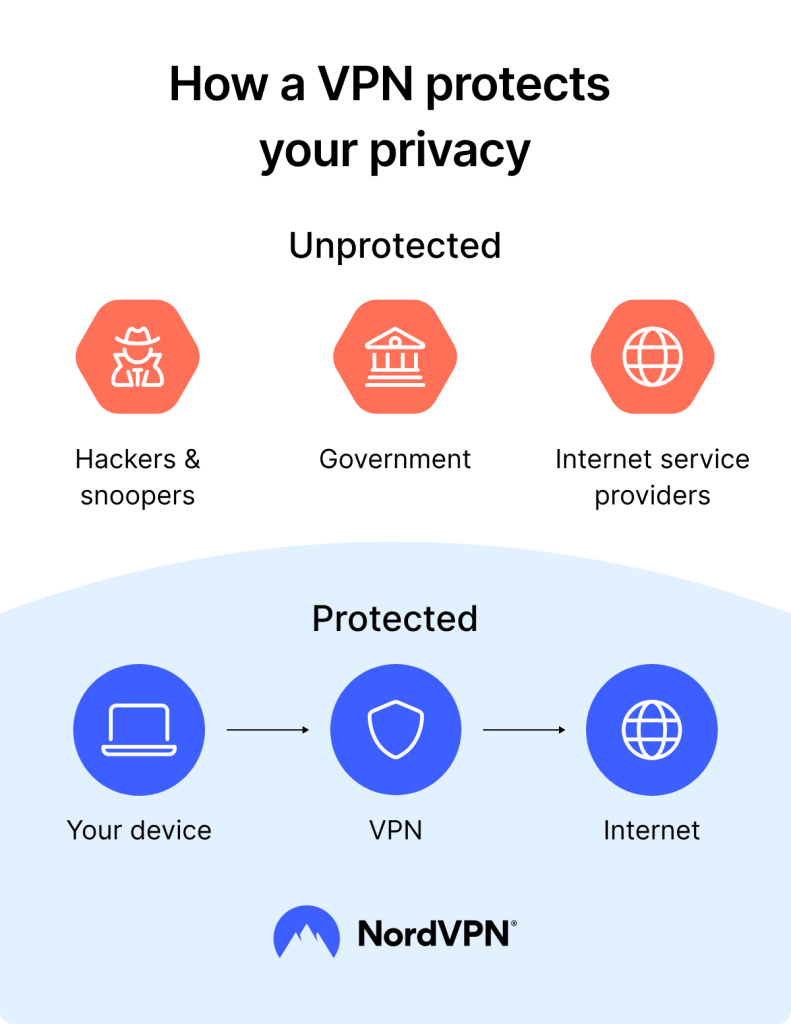
VPNs shield internet traffic from prying eyes using encrypted tunnels—but the longevity of that protection depends on the hardness of its underlying mathematics. Anyone who intercepts encrypted VPN traffic today could “store it now, decrypt later” once quantum technology matures—a major risk for:
- Governments, militaries, and intelligence agencies.
- Healthcare, legal, and financial industries required to maintain privacy for years or decades.
- Individuals and organizations for whom privacy is a fundamental right or business need.
Post-quantum encryption (PQE), or quantum-resistant cryptography, is engineered to remain secure even if adversaries possess a powerful quantum computer in the future.
How Do PQ-Secure VPNs Work? The NordVPN Example
NordVPN is one of the first mainstream providers to publicly roll out post-quantum encryption for day-to-day users, integrating it into its NordLynx protocol (built atop WireGuard).
Under the Hood: Protocol Design
- Hybrid Key Exchange: When a VPN session begins, the software uses both a traditional method (like X25519 or fast ECC) and a post-quantum algorithm (such as Kyber, a lattice-based algorithm selected by NIST for post-quantum standards). The two keys are mixed, so breaking the encryption would require defeating both cryptosystems simultaneously.
- Seamless Integration: The implementation is designed to be “toggle-on” simple—users don’t need to understand quantum physics to benefit. The app negotiates a session using both classical and PQ algorithms without visible complexity.
- Hardware and Performance: The PQ algorithms NordVPN employs are designed for minimal overhead. Benchmarks suggest negligible impact on connection speeds for most users, with optimization happening at the protocol level to compensate for the modest increase in handshake complexity.
Scope and Compatibility
- Supported Platforms: NordVPN launched PQE for Linux as a preview and has now extended it to Windows, macOS, Android, iOS, Android TV, and tvOS via the WireGuard-based NordLynx protocol.
- Limitations: PQE is only available on NordLynx connections, and doesn’t (yet) support every feature, like Meshnet (for private device-to-device connectivity) or obfuscated servers (for bypassing firewalls and censorship).
- Standards and Transparency: NordVPN utilizes NIST-endorsed cryptographic standards, continuously updating its stack as new insights and algorithms are validated by the cryptographic community.
Deep Dive: The Advantages of PQ-Secure VPNs
- True Future-Proofing: By using hybrid cryptography, VPN providers can guarantee that even intercepted traffic today will be unreadable by quantum adversaries in the future.
- Granular Security Assurance: Organizations with strict compliance mandates—GDPR, HIPAA, or governmental directives—gain peace of mind that they are ahead of regulatory timelines, securing customer and citizen data for years ahead.
- Trust Partitioning: If one layer of encryption (either traditional or PQC) is ever compromised, the other still stands. This “belt and suspenders” approach buys time in a rapidly shifting threat landscape.
- No User Disruption: Security upgrades occur without requiring users to change their workflows, hardware, or understanding of cryptography.
Challenges and Limitations—Don’t Ignore These!
- Algorithmic Uncertainty: Even though NIST’s candidates are extensively peer-reviewed, post-quantum cryptography as a field is still new and evolving. Algorithms may need patching or even withdrawal as further cryptanalysis matures.
- Performance Cost: PQ algorithms, especially in their non-optimized early forms, can require more CPU cycles and memory than classical ones, though the impact for most VPN users is small thanks to optimizations in protocols like WireGuard/NordLynx.
- Legacy Infrastructure: Network equipment, legacy applications, and IoT gadgets often lack the computing resources (or firmware update cycles) needed to implement new crypto, slowing industry-wide transitions.
- Partial Adoption: Many VPN features—like multi-hop, split tunneling, or custom protocol stacks—are not yet universally compatible with PQ cryptography. A staged rollout means users should double-check where PQE is actually active.
The Big Picture: Why Should You Care?
Quantum attacks are not decades away—they’re relevant now due to the “store now, decrypt later” threat model. Post-quantum cryptography is a crucial, proactive step for anyone whose privacy, business, or compliance depends on data remaining secret in years to come. This includes:
- Journalists in authoritarian countries.
- Enterprises handling long-lived private customer records.
- Governments and critical infrastructure providers.
- Everyday users who want their private moments to stay private—now and in the future.
The Future: What’s Next for Post-Quantum Secure VPNs?
The arms race between cryptographers and attackers is perpetual. As quantum hardware advances, crypto standards, including PQE, will need continual re-evaluation and upgrades.
- Standardization: NIST and international bodies are finalizing standards and best practices, which will be adopted across commercial VPNs and open-source projects.
- Automated Key Updates: Future VPN clients might automatically shift PQC algorithms as new standards emerge, much like how TLS and browser cryptography have evolved.
- Universal Encryption: Eventually, PQC integration will become default in all privacy tools—VPNs, messaging apps, secure email—creating a global, quantum-resilient privacy layer.
- Cloud and Enterprise Uptake: Cloud service providers and business VPNs will likely accelerate PQC rollout, servicing industries with decade-long confidentiality requirements.
The bottom line:
Quantum computing’s threat is not distant—its implications are shaping internet standards today. With robust, hybrid post-quantum encryption, VPNs like NordVPN are providing the first line of defense for global privacy and data protection—building resilience into our core internet infrastructure before the quantum future makes current encryption obsolete.

0 Comments
Most Voted