-

Mastering Big Data with Hadoop: A Comprehensive Guide to DevOpsSchool’s Certification Course
In today’s data-driven world, where petabytes of information are generated every second, organizations are racing to harness the power of…
-

Mastering the Future: An In-Depth Review of DevOpsSchool’s Master Artificial Intelligence Course
The world is accelerating into an era defined by data and intelligent systems. Artificial Intelligence (AI) is no longer a…
-

Mastering AppDynamics: Your Gateway to Advanced Application Performance Management
In today’s fast-paced digital landscape, where applications are the heartbeat of businesses, ensuring optimal performance isn’t just a nice-to-have—it’s a…
-

Master Linkerd: Transform Kubernetes Networking
Linkerd is rapidly becoming the heartbeat of service mesh solutions for cloud-native and Kubernetes architectures. This ultralight CNCF-hosted tool empowers…
-

DevOpsSchool’s Certified Kubernetes Administrator Training: Why It’s Essential for DevOps Professionals
Mastering Kubernetes has become an indispensable skill for any modern DevOps engineer. The Certified Kubernetes Administrator (CKA) program from DevOpsSchool…
-

Unlock Your IT Potential: A Deep Dive into DevOpsSchool’s ITIL® Certification Training
In today’s fast-paced digital landscape, IT isn’t just a support function; it’s the core engine of business growth. To keep…
-

The Ultimate Guide to DevOpsSchool Certifications
In the fast-paced world of software development and IT operations, staying ahead means embracing continuous learning and specialization. As organizations…
-

Path to HashiCorp Vault Mastery and Certification
In today’s rapidly evolving digital ecosystem, where data breaches can cripple organizations overnight, the role of secrets management has never…
-

Unlock the Secrets of Secrets Management: A Deep Dive into the HashiCorp Certified Vault Training
In today’s fast-paced, cloud-native world, security is not just an afterthought—it’s the bedrock of any successful digital infrastructure. At the…
-
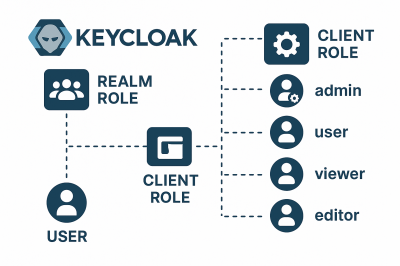
What is a Client Role in Keycloak?
In Keycloak, clients represent applications or services (like APIs, admin dashboards, or web apps) that want to use Keycloak for…